Within a few days of releasing thePurge, strata decided to release yet another VM! This one was called theFrequency… It presents a very nice challenge involving radio signal encoding and audio stego. I needed several hints to solve this one, but it was worth it!
I downloaded it and did the normal nmap dance. Like many VMs these days, only one port was open. It was, of course, http, serving only a single mp3 file:

DA-DIT-DA
It’s some kind of ambient mix, but at certain points in the audio you can hear weird noises and clicks. This sounded like audio stego to me! After downloading, I fired up Sonic Visualizer and loaded the mp3. Select ‘Layer > Add spectrogram’ or press Ctrl+G to visualize the sound. Right away, we can hear/see something that can only be Morse:
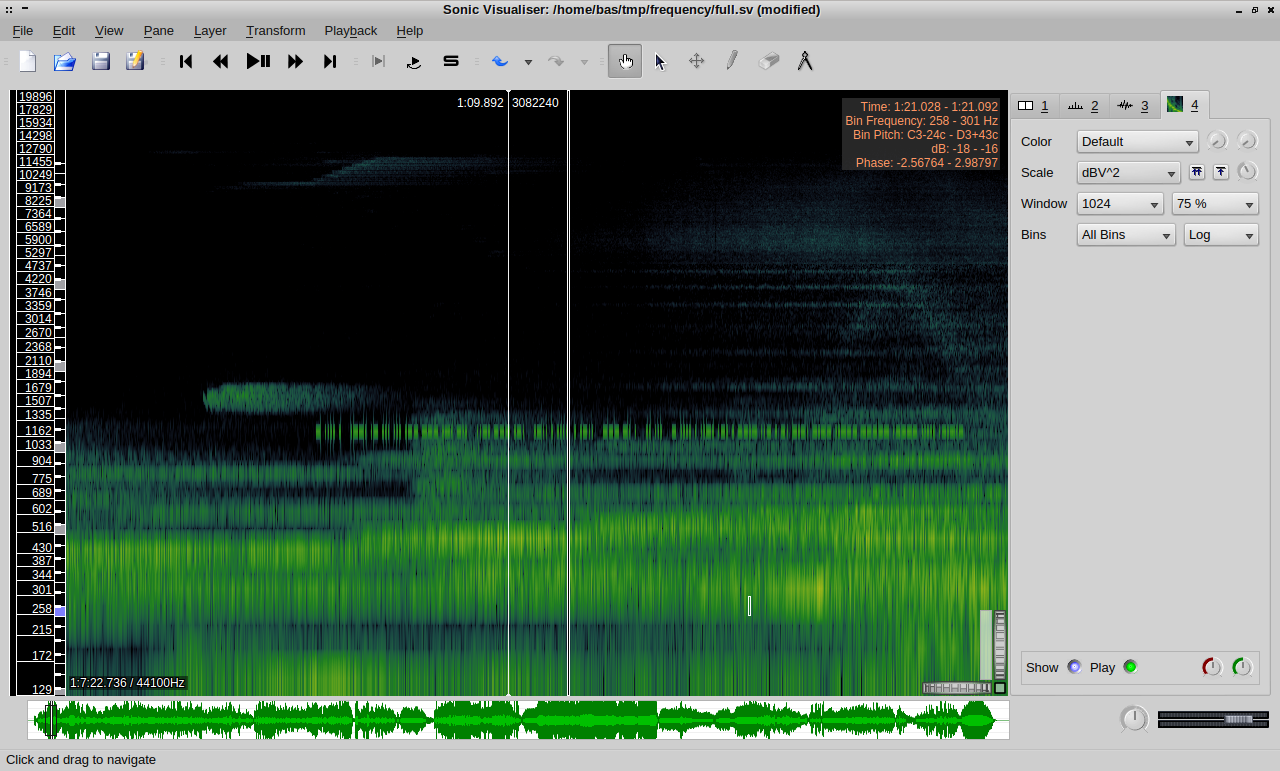
I just used a Morse lookup table to decode it by ear/hand:
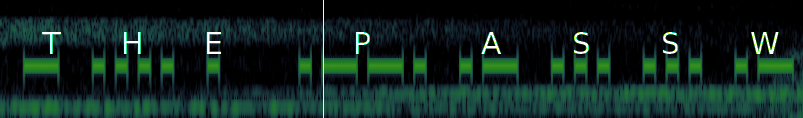
It decoded to THE PASSWORD FOR LEVEL ONE IS THEFREQUENCY2015. I then tried to use ssh to login to VM, only to be rejected. I had to use sftp, apparently. After logging in with lowercase thefrequency2015., I grabbed the only file that was present. This was part of a larger SSH key. Gotta catch ‘em all!
LIGHTWRITER
The second series of clicks is further away in the audio, at around 17 minutes. Looking at the spectrogram:
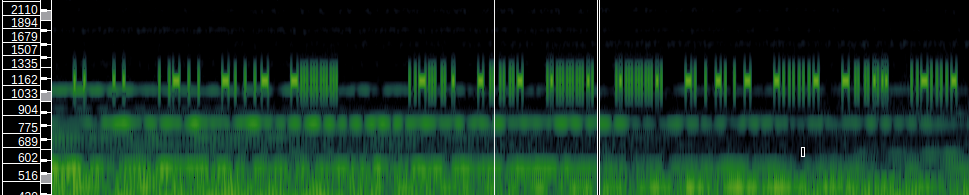
I couldn’t really figure out what this was. strata gave two hints, being this page full of digital radio mode examples and saying something like ‘you can almost read the letters’. This meant that it had to be Hellschreiber (German for Lightwriter, I believe). But I couldn’t figure out how to decode it by hand in Sonic Visualizer. I got pretty close:
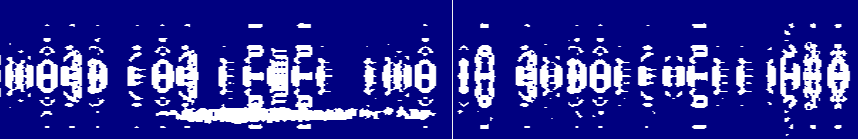
I could barely make out THE PASSWORD FOR LEVEL TWO IS and then… I started looking at the symbols, some looked very similar. I started seeing some letters. Looking at the Hellschreiber wikipedia page, it turned out Hellschreiber was invented by Rudolf Hell. This was also the password; I finally managed to decode it to RUDOLFHELL1920.
Then I managed to install fldigi on an Ubuntu 12.04 VM. This made it significantly easier. I extracted the relevant part of the mp3 with audacity and merged the stereo channels to mono (otherwise fldigi complains).
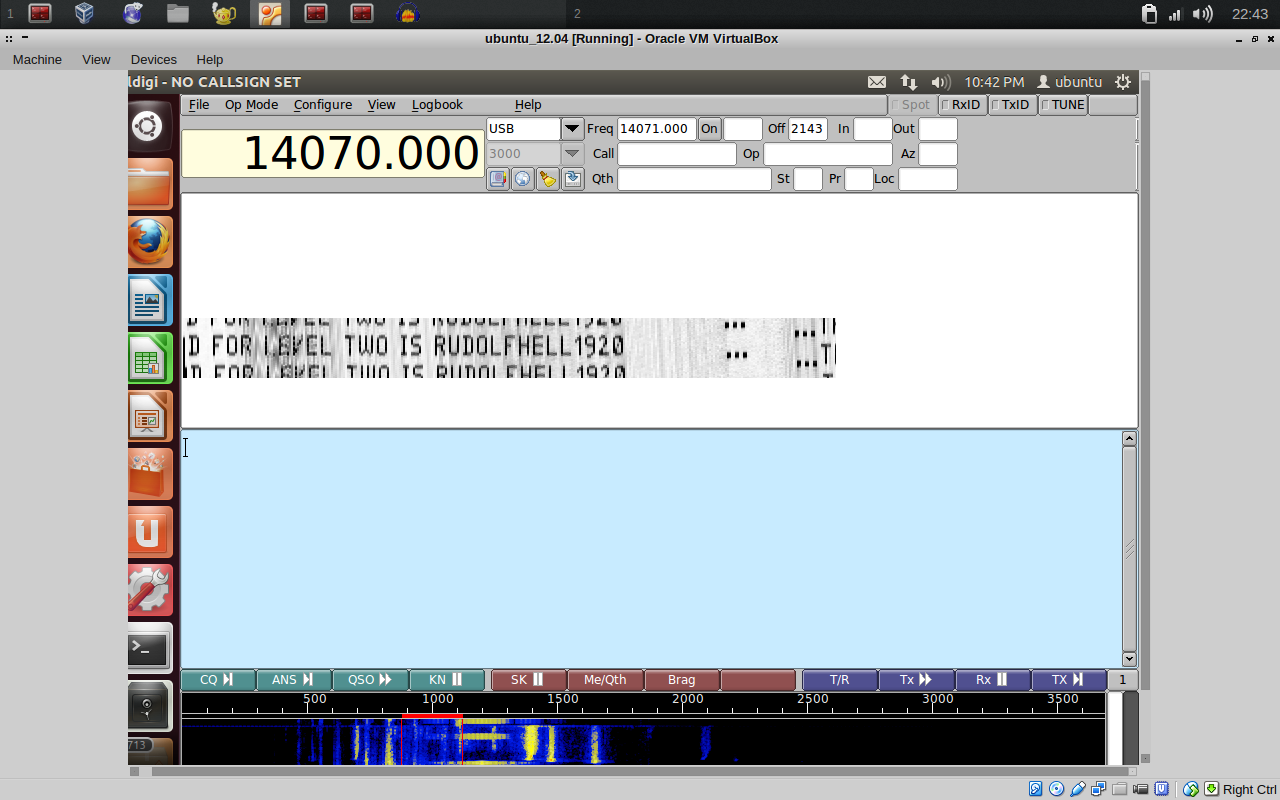
Again I could sftp to the VM and grab part of the key.
IT SOUNDS JUST AS BAD AS IT LOOKS
Onto level three! It sounds warbling, almost dissonant (for those of you that read Stephen King, “It sounds Hawaian, doesn’t it?”). You can find it around 30:40, and from the digital modes page earlier, I thought that it was RTTY. It sure sounded like it! fldigi did not agree. It turned out to be BPSK31:
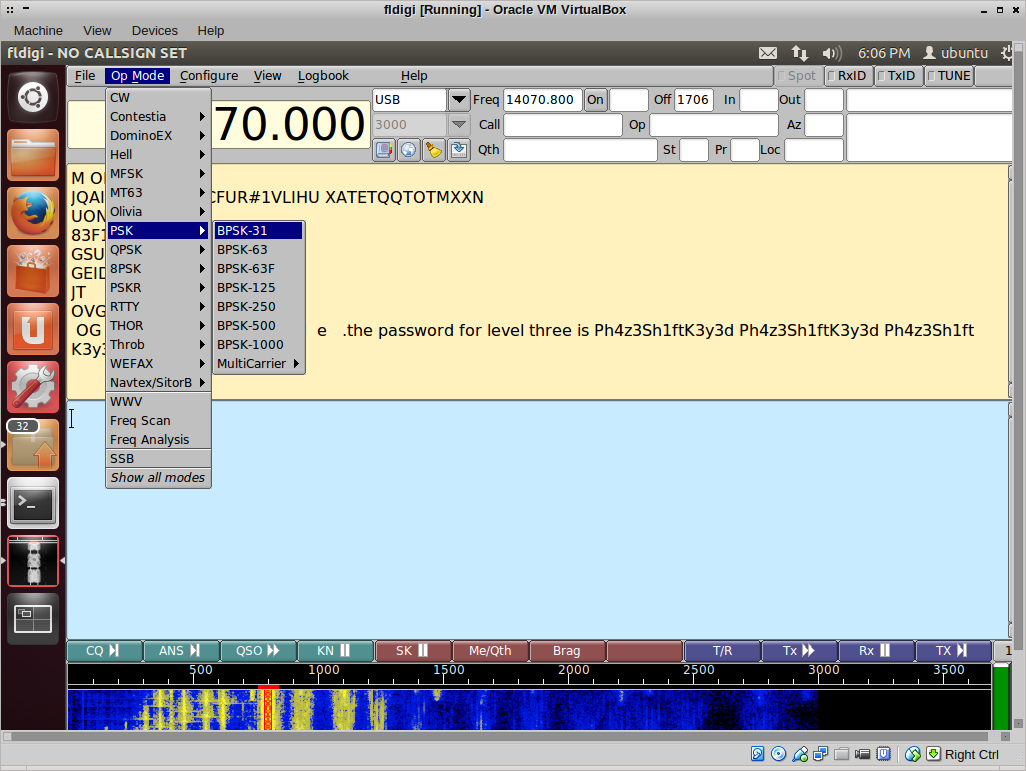
The key was coming together now. Level four was found around 41 minutes and sounded even worse. I had no idea how to decode it, but luckily strata gave me a hint. The bandwidth on this audio encoding scheme was 2 kHz and I tried all the modes that allowed for this bandwidth. It was the MT63 mode, used also by emergency services. You have to keep the sample running for a while, as only the first part really contains information.
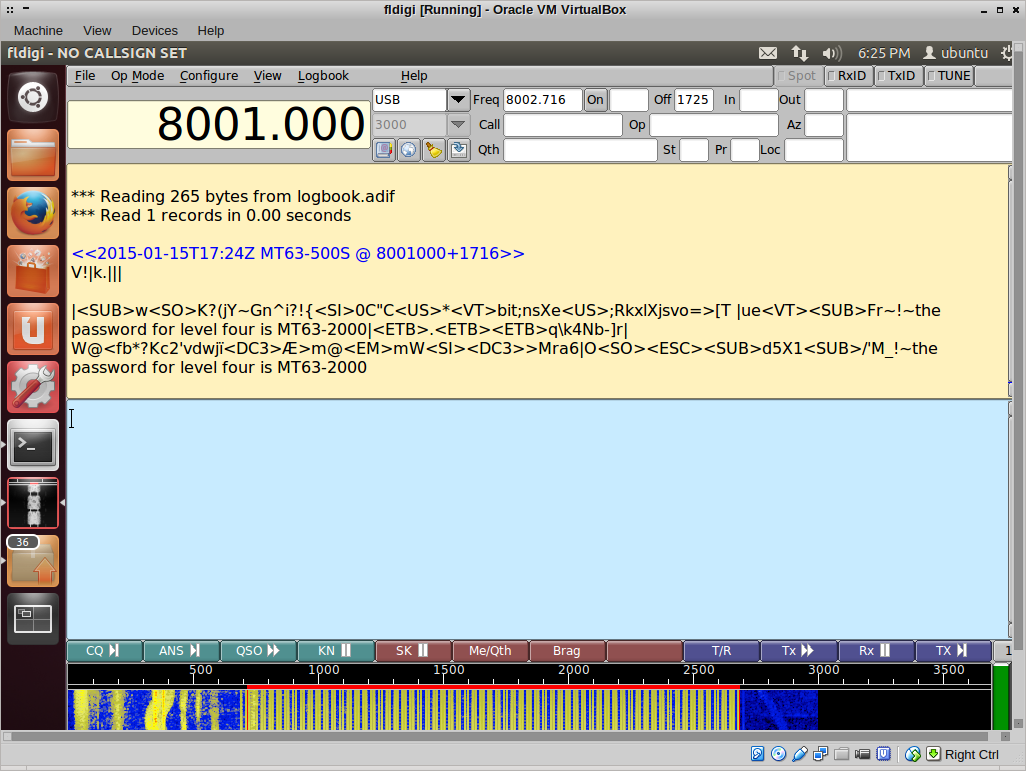
Level five was next, and turned out to be RTTY!
I could actually hear this, also for the next one. Level six was THROB and that describes the sound quite accurately.
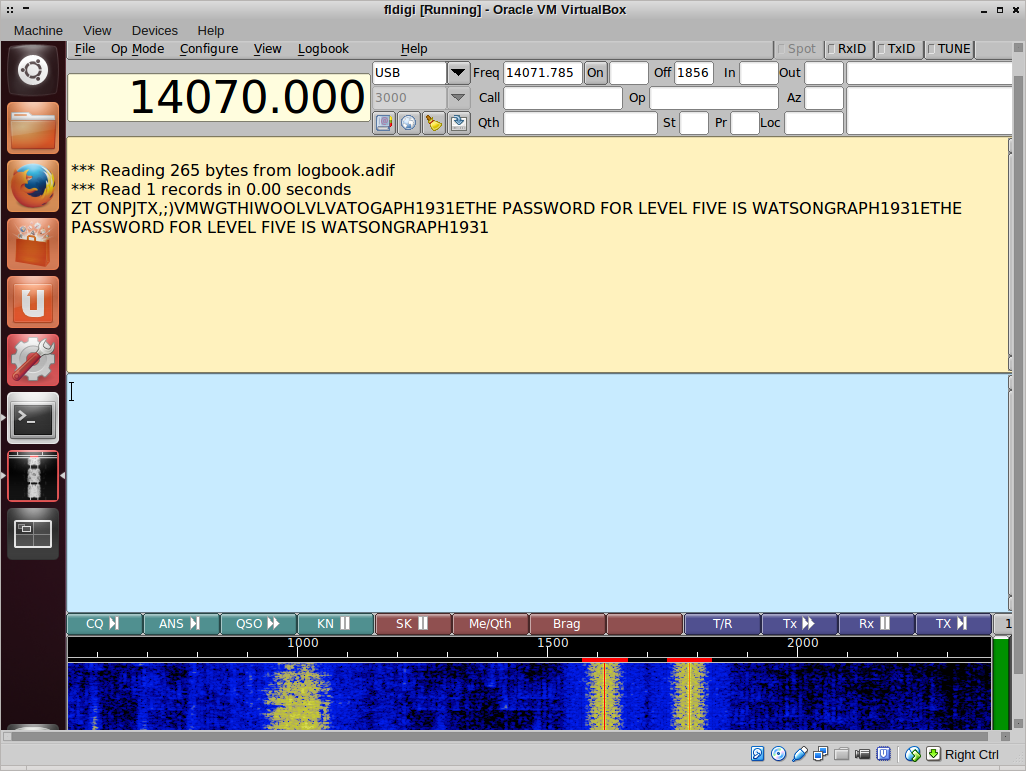
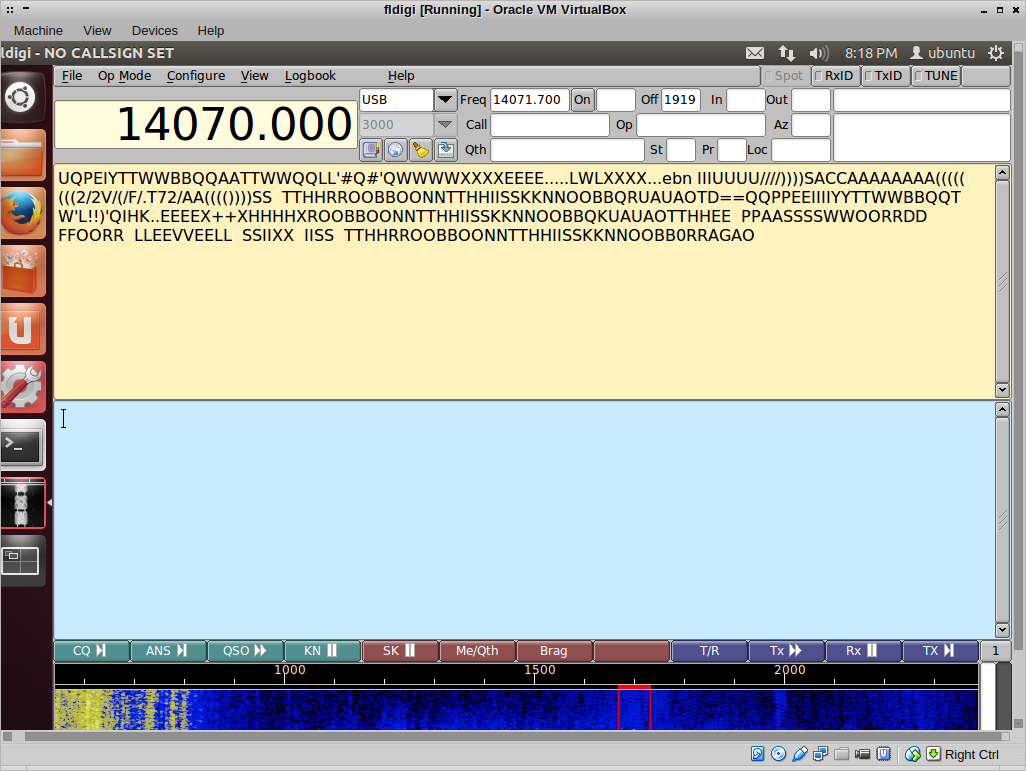
So now I had all the pieces of the key! I pieced them together and threw them at the root login… only to be asked for a passphrase. Bah! I thought, back to the mp3 and look for the passphrase. I looked at level six again:
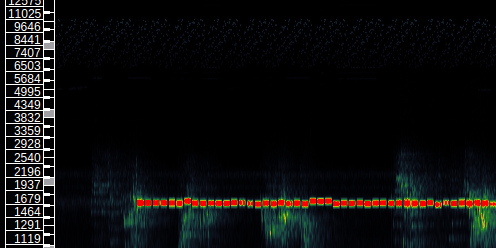
There seemed to be something at around 8 kHz! I stumbled upon this page which made me believe it was encoded using olivia or contestia. I extracted that piece, applied a high-pass filter with a cutoff around 6 kHz and amplified the signal. But I could not get fldigi to decode it. After consulting with strata, it seemed that this was actually part of the ambient mix itself. Talk about stego!
So now what? I had to update my ssh to go login. The version on my own box did not support the key format. I opened a Kali box, got the latest & greatest source tarball for OpenSSH, which was version 6.7p1. After that was done compiling, I could login as root using the acquired private key.
Victory at last
1 2 3 4 5 6 7 8 9 10 | |
Learned a ton while doing this one, very left-field VM, very different from the usual VMs on VulnHub! Overall, I’d say it’s perfect material for CTF training!