For this challenge, we had to decode a ton of QR images given to us via a nc connection for 70 points. Sounds like fun!
Upon connecting to the service, it tells us we need to decode as much flags as we can. We also get the first flag.
 Right, so I turned to the solution to QR Garden by Swappage. I liked his approach and decided to do something similar. I installed
Right, so I turned to the solution to QR Garden by Swappage. I liked his approach and decided to do something similar. I installed zbar on my box and cobbled together a python script. That script would connect to the QR service, write out the QR code to disk using PIL and then call zbarimg to decode the QR code. I had some issues at the start because I mixed up the colors of the QR code, but then I was decoding them all pretty rapidly.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 | |
The script was receiving and decoding QR codes quite rapidly, but I didn’t receive any flags. I finally just fired up wireshark to grab the flag from the TCP stream:
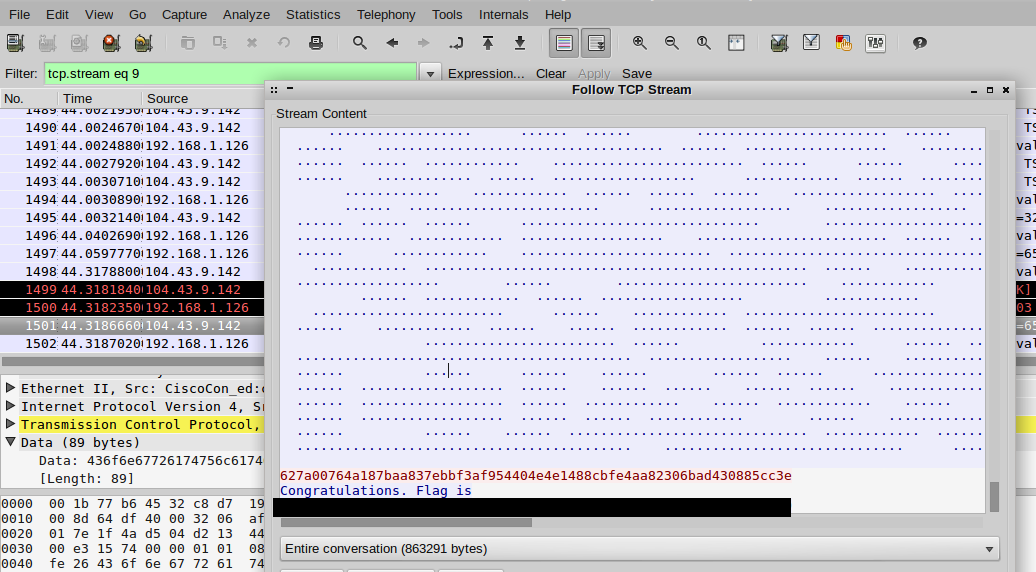
Not the most elegant way to grab the flag, but hey, it worked.